Storage
To save the processing results logs, liveness assessment data (if using the Liveness module), and identification binary data (if using the Identification module), you need to configure storage. For a detailed guide on setting up storage, see Configuration.
The supported storage options are the following:
Info
You can find more information about each cloud storage type by navigating to the following links: Azure Blob Storage, Google Cloud Storage, AWS S3.
For access management, we support Workload Identity Federation; see links with configuration instructions in the table below.
| Storage | Configuration instructions |
|---|---|
| Azure Blob Storage | Azure AD Workload Identity Documentation Support Azure Workload Identities |
| Google Cloud Storage | Authenticate to Google Cloud APIs from GKE workloads |
| AWS S3 | EKS Pod Identities IAM roles for service accounts |
File System (FS)
Note that if you use Network file storage, you need to mount them as local drives.
Azure Blob Storage
To authenticate and access Azure Storage in your application, you can use one of the following authentication methods.
- Standard authentication via environment variables: Refer to the official Azure documentation for instructions.
- When running in an Azure environment and assigned the appropriate role with Azure Storage access rights, authentication is enabled.
Note
Both methods described above require the storage account to be specified in the storage.type.az.storageAccount field.
- Alternatively, you can authenticate to Azure Storage using a connection string that should be set in
storage.type.az.connectionString. The connection string contains the necessary information to establish a connection to the storage account. Here's an example of a connection string:
storage:
type: az
az:
storageAccount: <AZURE_STORAGE_ACCOUNT>
connectionString: "<DefaultEndpointsProtocol=http;AccountName=devstoreaccount1;AccountKey=lkschfs7lkfhdyhcbdsk548weksdhc4ksdjvg473239orhfsdjfhsd7kfhfkue/C2RTGHYPui/LPSBnksoMKGw==;BlobEndpoint=http://{hosts['azure']}:10000/devstoreaccount1;>"
Make sure to replace {hosts['azure']} in the connection string with the appropriate hostname or IP address of your Azure Storage account.
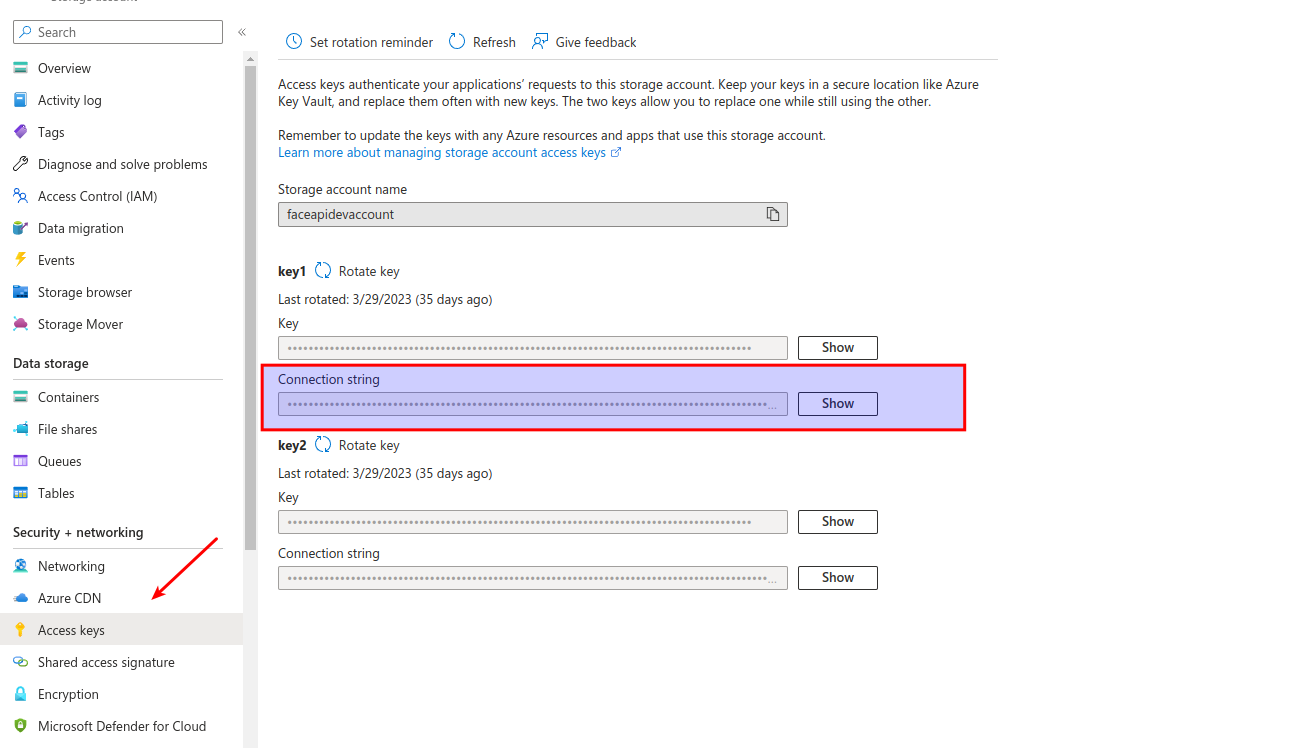
You can find the connection string in the Access keys section of your Azure Storage account:
Google Cloud Storage
To enable Google Cloud Storage, follow the official Google documentation.
Permissions
For the required Google Cloud Platform permissions, see the table below.
| Bucket permission name | Description |
|---|---|
storage.buckets.get |
Read bucket metadata, excluding IAM policies, and list or read the Pub/Sub notification configurations on a bucket. |
storage.objects.create |
Add new objects to a bucket. |
storage.objects.delete |
Delete objects. |
storage.objects.get |
Read object data and metadata, excluding ACLs. |
storage.objects.list |
List objects in a bucket. Also read object metadata, excluding ACLs, when listing. |
storage.objects.update |
Update object metadata, excluding ACLs. Also read object metadata, excluding ACLs, when updating. |
Descriptions are taken from the IAM permissions for Cloud Storage article.
AWS S3
To authenticate and access AWS S3 storage in your application, you can configure it using one of the following methods:
- By setting credentials via a YAML file
- Via the standard AWS envs: https://docs.aws.amazon.com/cli/latest/userguide/cli-configure-envvars.html
- By running the application within the AWS environment and assigning the necessary IAM role to your application with the required permissions to access S3
Note that MinIO storage is utilized for on-premises installations within our containers. It is compatible with AWS S3 and is configured in the same way.
Permissions
The following permissions are required:
s3:PutObjects3:PutObjectAcls3:GetObjects3:GetObjectAcls3:DeleteObjects3:ListObjects
Here is an S3 policy example:
{
"Version": "2012-10-17",
"Statement": [
{
"Action": [
"s3:ListBucket",
"s3:GetBucketLocation"
],
"Effect": "Allow",
"Resource": [
"arn:aws:s3:::regula-test-permissions-bucket"
]
},
{
"Action": [
"s3:PutObject",
"s3:PutObjectAcl",
"s3:GetObject",
"s3:GetObjectAcl",
"s3:DeleteObject"
],
"Effect": "Allow",
"Resource": [
"arn:aws:s3:::regula-test-permissions-bucket/*"
]
}
]
}